Viewing Event Logs
Event logs must be
viewed with regularity for auditing to have any effect. To view the
security log, open Event Viewer from the Administrative Tools folder and
then click Security. Double-click any entry to see more information
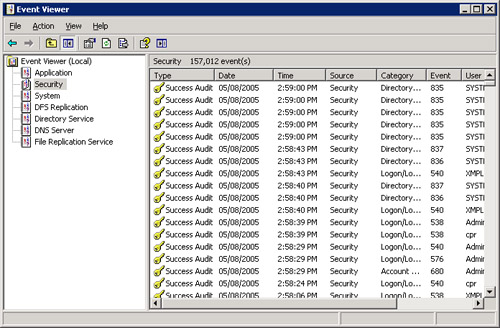
about it. The security entries in Figure 3
occurred in the span of about a minute because the object being audited
was set to audit successful events. Of course, you’ll generally learn
more from auditing failed events than from auditing successful ones, but
this does demonstrate the need to choose your auditing battles
carefully.
Searching Event Logs
No
matter how selective you are, the event logs will mix all sorts of
information together, making searches for specific information
difficult. To search for a specific type of event, select the log in
Event Viewer, and choose Find from the View menu. In the Find dialog
box, shown in Figure 4, select the type or types of events you want returned. Table 3 describes the filtering options for the event logs.
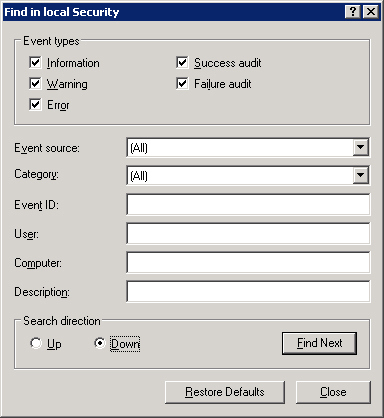
Table 3. Options for filtering event logs
| Option | Use to Search or Filter for |
|---|
| Information | Notification that some major operation has been performed successfully. |
| Warning | Notification
of some problem or potential problem. Warnings might or might not be
significant. For example, replication performed after repeated tries
will generate a warning. |
| Error | Notification
of an important event. Errors signify a loss of data or a loss of
function. For example, failure of a service to start during bootup will
generate an error. |
| Success Audit | Events audited for success. |
| Failure Audit | Events audited for failure. |
| Event Source | A source for an event, such as a system component or a program. |
| Category | Events by category, such as logon/logoff, policy change, or process tracking. |
| Event ID | The specific ID number assigned to each logged event. |
| User | A specific user. |
| Computer | A specific computer. |
| From | Events
after a specific date. The default is the first date in the log. You
can click the drop-down box to select events on a specific date. |
| To | Events before a specific date. The default is the last date in the file. |
Filtering Event Logs
If
you don’t have enough specific information to locate what you need, you
can filter an event log for certain types of information. To use event
log filtering, follow these steps:
1. | Launch Event Viewer from the Administrative Tools folder.
|
2. | Right-click the log you want to search, and choose Properties from the shortcut menu.
|
3. | Click the Filter tab. Table 3 describes the fields in this tab. Click OK when you’re ready to start filtering.
|
4. | The log appears, filtered as you requested. To view the full, unfiltered log again, return to the Filter tab and click Clear.
|
Setting the Size of Event Logs
When an event log is full,
a dialog box pops up to notify you. If this happens often, you might
want to reduce the number of items being reported or increase the size
of the log. To set event log options, follow these steps:
1. | Launch Event Viewer from the Administrative Tools folder.
|
2. | Right-click the log you want to configure and choose Properties.
|
3. | In the General tab, set the options you want. Under When Maximum Log Size Is Reached, there are three options:
- If you don’t archive this log, select Overwrite Events As Needed.
- If you archive this log at regular intervals, you can
select the Overwrite Events Older Than option. Fill in the appropriate
number of days.
- Do Not Overwrite Events, the last option, means that
the log must be cleared manually. When the maximum log size is reached,
new events are simply not recorded.
|
4. | Click OK when you’re finished.
|
Note
To set limits for a large number of machines—a department or a whole domain—use Group Policy.
|
Maybe you are so
security-conscious that none of the event log options are acceptable. If
you absolutely, positively must not lose a single security event, you
can set the computer to halt when the security log is full. A registry
change is necessary to make this happen. First, set Event Log Wrapping
to either Do Not Overwrite Events or Overwrite Events Older Than n
Days. Then start Regedit.exe, proceed to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\CrashOn
AuditFail, and change the value to 1.
This setting takes effect
after a reboot; then, when the log is full, the system simply stops.
After restarting, only administrators are able to log on until the
security log is cleared. This is obviously a drastic measure, but if you
absolutely must retain an audit trail on a particular server, this is
one way to ensure that.
|
Archiving Event Logs
If you will be using event
logs to track system usage trends, you must save them. To archive an
event log, launch Event Viewer from the Administrative Tools folder and
click the log you want to archive. Then, from the Action menu, choose
Save Log As. If you save the file in the event log format (.evt), it can
be reopened in Event Viewer, and all the binary data for each event is
retained. You can also save logs as .txt files or in comma-delimited format (.csv), but in those cases the binary data isn’t saved.